8. Setting up HTTPS¶
8.1. Preface¶
Cases shared by Intella Connect can be accessed in various ways in the browser (the addresses listed below are artificial):
- via an internal IP, e.g. http://192.168.1.104:8084
- via an external IP, e.g. http://91.100.40.80:8084
- via a domain name, e.g. http://this-is-my-domain.com:8084
- via a machine’s network name, e.g. http://my-PC:8084
The HTTPS (SSL) communication layer needs to know under which URL Intella Connect’s pages will be served. Knowing that and having a proper certificate validated by a third party vendor (called a Certification Authority) will allow Connect to make use of a secure channel for serving these pages.
Note: SSL 3.0 is no longer supported, to protect against the POODLE attack.
8.2. Prerequisites for HTTPS configuration¶
There are a number of things that need to be done before you can use HTTPS in Intella Connect. Please make sure that all of these requirements are met.
8.2.1. Signed SSL certificate¶
These steps depend on whether you already have a working SSL certificate, so please follow the steps most suitable for your situation.
I’m already in possession of an SSL (PKCS12) certificate issued for my company/domain
- Read the locating the utility program for working with keystores section of this document to learn how to make use of the keytool utility.
- Import the existing PKCS12 file called
xxx.p12into a new keystore: >keytool -importkeystore -srckeystore xxx.p12 -srcstoretype PKCS12 -destkeystore my-site.com.keystore - At this point you will have a new keystore database containing your private and public keys.
- The next step depends on whether or not the .p12 file contains required certificates:
- If the .p12 file contains all the needed certificates, please proceed with the modifying SSL settings in Intella Connect Dashboard section.
- If the .p12 file did not contain all the necessary certificates from your CA, please download them and proceed with the adding certificates to the Keystore section of this document.
I do not have a SSL certificate or I want to use a new one
- Decide upon the Case URL scheme that you would like to use for case sharing in Connect. Your options are:
- A domain (recommended) – domain names are easier to remember and do not change that often. If your domain is already taken, you can easily choose something unique, yet easy to remember, like: www.my-connect-cases.com
- A public IP address.
- Sign up with one of the Certification Authorities and open an account that will allow you to sign domain (or IP) certificates.
- Remember the address for which the certificate was issued.
8.2.2. Configuring the domain¶
If you decided to use a domain for case sharing, then you need to configure it now. Please log in to the machine (server) where you will be running Connect and check its public IP (when in doubt, please use Google).
After that you need to log in to the management panel for your domain provider and set the DNS records so that the domain points to the current public IP of your Connect PC.
Note: for purposes of this tutorial we will be using an artificial address/domain pair: 1.2.3.4, www.my-site.com
8.2.3. Configuring the router (optional)¶
It might happen that the server machine is behind NAT, managed by a router. In that case you will need to set up port forwarding for a TCP port used by Intella Connect.
8.3. Setting up SSL certificates in Connect¶
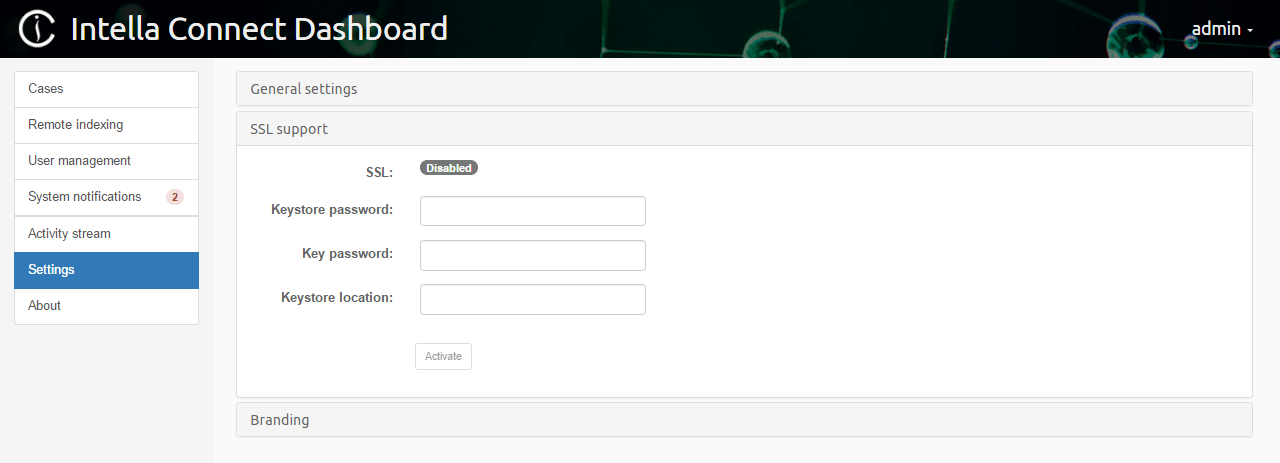
On the Intella Connect Dashboard page, after clicking on the Settings menu item, one can see the following configuration panel:
The most important thing to notice here are the properties of the so-called Keystore. A keystore is nothing more than a secure database that holds all the certificates needed by a server (in our case - Connect). In order to proceed, we will need to create the keystore manually.
8.3.1. Locating the utility program for working with keystores¶
Intella Connect bundles a special utility program for working with keystores. This tool is a part of the bundled Java distribution and is called keytool.exe. It can be found in:
C:\Program Files\Vound\Intella Connect 1.8\jre\bin\keytool.exe
8.3.2. Creating a new keystore¶
First, let’s prepare a directory to work with. For the sake of this
manual, I have created the folder C:\Users\Lukas\Desktop\ssl where I will be
temporarily storing all the necessary files.
Note: if you have your own certificate, you do not need to generate the private/public key pair in this step (note the-genkeyflag) and you can safely proceed to the adding certificates to the Keystore section.
To create a keystore, please do the following:
- Open a command line tool by pressing *Windows + R* and typing *cmd* followed by *Enter*.
- Use the *cd* command to go to the folder containing the keystore application.
- Enter the following command (put everything on a single line, change
folders if needed):
keytool -genkey -keyalg RSA -keysize 2048 -keystore C:\Users\Lukas\Desktop\ssl\my-site.com.keystore - You will be asked to enter some values. Please use your best judgment to fill in the necessary fields. Listed below are the ones that are important for Connect:
- Keystore password: use a strong password, we will be using it later in the Settings panel.
- First and last name (also referred as CN – Common Name): please provide the address for which the certificate was issued to (remember: that was either a public IP or domain).
- Key password: this password is different from the keystore password. Use an equally strong password.
- After this step you should have a new keystore ready with an unsigned
certificate. The keystore is located in the folder used for temporary files, in this example
C:\Users\Lukas\Desktop\ssl\my-site.com.keystore.
8.3.3. Requesting certificate signature¶
Note: this and the following steps apply only if you did not have your own certificate already and you have just created one in the step before.
Since now you are in possession of an unsigned certificate, you need to ask a Certification Authority (CA) to sign it. CAs accept only requests for certificate signature, so you need to create one using the keytool.
On the command line, please enter the following command:
keytool -certreq -keyalg RSA -file
C:\Users\Lukas\Desktop\ssl\my-site.com.csr -keystore
C:\Users\Lukas\Desktop\ssl\my-site.com.keystore
You will be asked for the master password for the keystore, which you
have defined in the first step. This should produce a file called
my-site.com.csr
8.3.4. Signing the certificate¶
You now have to supply this signature request to the Certification Authority. This process is specific to the authority signing the certificate. After the CA is done with processing your request, you should receive a set of signed (verified) certificates, which can now be added back to the keystore.
8.3.5. Adding certificates to the Keystore¶
You now have to add each certificate that you have received from
your CA back to the keystore. Most likely you have received three files:
the CA’s certificate, an intermediate certificate and the one which
applies to your domain (IP). Please use keytool.exe again to add them
using the commands below. Please keep in mind, that for this tutorial
our CA has supplied us with three files (AddTrustExternalCARoot.crt,
PositiveSSLCA2.crt and www_my-site_com.crt) which are stored in
the “signed” subdirectory:
keytool -import -trustcacerts -alias
AddTrustExternalCARoot -file
C:\Users\Lukas\Desktop\ssl\signed\AddTrustExternalCARoot.crt
-keystore C:\Users\Lukas\Desktop\ssl\my-site.com.keystore
keytool -import -trustcacerts -alias PositiveSSLCA2
-file C:\Users\Lukas\Desktop\ssl\signed\PositiveSSLCA2.crt
-keystore C:\Users\Lukas\Desktop\ssl\my-site.com.keystore
keytool -import -trustcacerts -alias mykey -file
C:\Users\Lukas\Desktop\ssl\signed\www_my-site_com.crt -keystore
C:\Users\Lukas\Desktop\ssl\my-site.com.keystore
8.4. Modifying SSL settings in Intella Connect Dashboard¶
At this point you can come back to the Intella Connect Dashboard page and finish setting up SSL. The three mandatory fields that are listed there should be set as following:
- Keystore password – the master password for the Keystore database.
- Key password – the password for our signed certificate.
- Keystore location – location of the Keystore, in this tutorial it
was:
C:\Users\Lukas\Desktop\ssl\my-site.com.keystore - Save the changes.
After that you need to restart Intella Connect to finish the process.
An appropriate warning about this should be displayed after you save the changes.
8.4.1. Setting up appropriate port¶
By default web browsers will try to connect to the 443 port when HTTPS protocol is used. Therefore if you configured Connect to listen on port 80, then you’ll have to change the port to 443.
8.4.2. Verifying HTTPS¶
In the end you should be able to navigate to https://www.my-site.com (note the “https” in the URL and lack of port) and see the Lock icon in the web browser’s address bar, which shows that you are using a secure connection.
After you log in into your dashboard, you may navigate to a shared case which should also be available using HTTPS protocol.
8.5. Troubleshooting issues with SSL¶
Before a certificate is trusted, browser must verify that the certificate comes from a trusted source. This verification process is called path validation. This involves processing public key certificates and their issuer certificates in a hierarchical fashion until the certification path ends at a trusted certificate. Typically this is a root CA certificate. If there is a problem with one of the certificates in the path, or if it cannot find a certificate, the certification path is considered a non-trusted certification path. A typical certification path includes a root certificate and one or more intermediate certificates.
If the browser shows certificate warning, please verify certificate chain by reading the keystore using 3rd party tool. See references section of Wikipedia article on keystore.
8.6. Disabling HTTPS¶
If SSL needs to be disabled, it can be done by clicking on the Disable button. This will however not remove SSL immediately. Intella Connect will only change the status of SSL to be disabled. The actual removal of the SSL channel will be performed when Intella Connect is re-started. This is to prevent any active users that use SSL from receiving errors related to the disabling of the SSL layer.
8.7. Modifying supported protocols and cipher suites (advanced)¶
If your security policy requires it, you may alter the way in which client and server communicate by specifying supported protocols and ciphers used. Intella Connect by default will not use SSLv3, relying on TLS instead. If you override supported protocols, please make sure to add “SSLv3” to the list.
The two settings that you can add to Intella’s Preferences are:
- ServerDisabledSslProtocols - a white-space separated list of DISABLED protocols. Defaults to “SSLv3”. Supported values are: SSL, SSLv2, SSLv3, TLS, TLSv1, TLSv1.1, TLSv1.2
- ServerEnabledSslCipherSuites - a white-space separated list of ENABLED cipher suites. Defaults to an empty string, which results in supporting a vast stack of around 80 common cipher suites. Supply your own list if you need to have more fine grained control over which ciphers to exclude.
More details about both protocols and cipher suites can be found here: http://docs.oracle.com/javase/7/docs/technotes/guides/security/StandardNames.html Please note that at the time of writing this manual specification required to support following ciphers:
- TLS_EMPTY_RENEGOTIATION_INFO_SCSV
- SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA
You can learn more about recommended cipher suites in this online reference: http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-52r1.pdf